How to manually remove the Yeabeasts.cc infection script from WMI
If you wish to remove the Yeabeasts.cc and TopYea infection, the easiest method is to use a program like Zemana. If you wish to remove this infection manually, though, you will need to use WBEMTest to delete the registered instance.
When starting WBEMTest we need to run it with administrator privileges. To do this, right click on the C:\Windows\System32\wbemtest.exe executable and then select Run as Administrator. WBEMTest will now start and you will see its main screen as shown below.
 WBEMTest
WBEMTestNow click on the Connect and in the Namespace field enter root\subscription as shown in the image below.
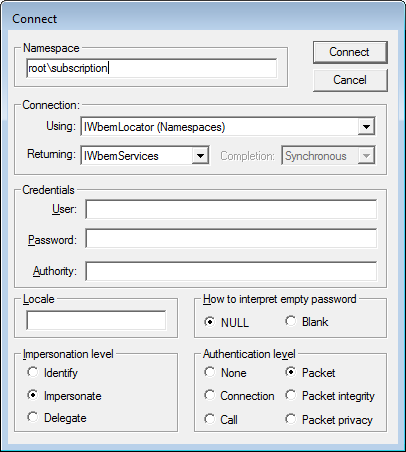 Connect to Namespace
Connect to NamespaceNow click on the Connect button. You will now be at the main WBEMTest options screen for the root\subscription namespace as shown below.
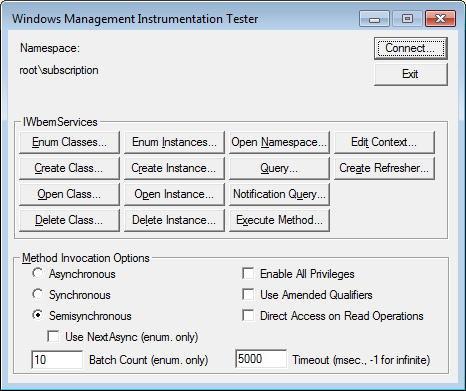 Subscription Namespace
Subscription NamespaceNow put a checkmark in the Enable All Privileges checkbox and click on the Enum Instancesbutton. This will open up a dialog box where it asks you to type in the name of the instance you wish to connect to.
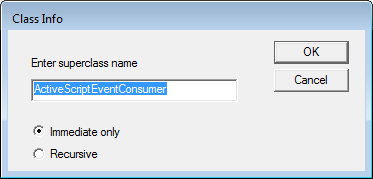 Class Info Dialog Box
Class Info Dialog BoxIn the above field, enter ActiveScriptEventConsumer and then press the OK button. You will now be at a page that lists all instances found for that superclass.
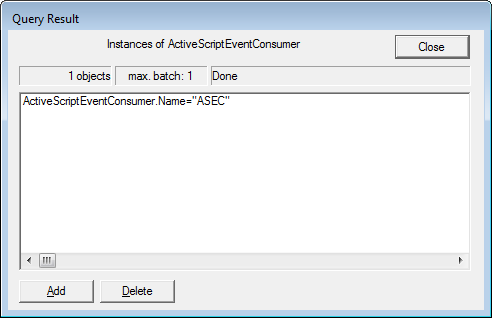 Query Result
Query ResultLook through the list of instances, and if you see one called ASEC, left-click on it once to select it. Then click on the Delete button.
The malicious event handler will now be removed from the WMI and you can use a tool like Shortcut Cleaner to clean your shortcuts of the Yeabests.cc and TopYea infection.
Este software limpou o registro:
Shortcut Cleaner 1.4.2 by Lawrence Abrams (Grinler)
Log:
Shortcut Cleaner 1.4.2 by Lawrence Abrams (Grinler)
Copyright 2008-2016 BleepingComputer.com
More Information about Shortcut Cleaner can be found at this link:
Windows Version: Windows 10 Home Single Language
Program started at: 08/27/2016 05:30:17 PM.
Scanning for registry hijacks:
* No issues found in the Registry.
Searching for Hijacked Shortcuts:
Searching C:\Users\Joao Lucas\AppData\Roaming\Microsoft\Windows\Start Menu\
Searching C:\ProgramData\Microsoft\Windows\Start Menu\
* Shortcut Cleaned: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Google Chrome.lnk => C:\Program Files (x86)\Google\Chrome\Application\chrome.exe --load-extension="C:\Users\JOAOLU~1\AppData\Local\kemgadeojglibflomicgnfeopkdfflnk"
http://yeabests.cc
Searching C:\Users\Joao Lucas\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\
* Shortcut Cleaned: C:\Users\Joao Lucas\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\Google Chrome.lnk => C:\Program Files (x86)\Google\Chrome\Application\chrome.exe --load-extension="C:\Users\JOAOLU~1\AppData\Local\kemgadeojglibflomicgnfeopkdfflnk"
http://yeabests.cc
* Shortcut Cleaned: C:\Users\Joao Lucas\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\Launch Internet Explorer Browser.lnk => C:\Program Files (x86)\Internet Explorer\iexplore.exe
http://yeabests.cc
Searching C:\Users\Public\Desktop\
* Shortcut Cleaned: C:\Users\Public\Desktop\Google Chrome.lnk => C:\Program Files (x86)\Google\Chrome\Application\chrome.exe --load-extension="C:\Users\JOAOLU~1\AppData\Local\kemgadeojglibflomicgnfeopkdfflnk"
http://yeabests.cc
Searching C:\Users\Joao Lucas\Desktop\
Searching C:\Users\Public\Desktop\
4 bad shortcuts found.
Program finished at: 08/27/2016 05:30:24 PM
Execution time: 0 hours(s), 0 minute(s), and 7 seconds(s)